ITSM Asset Management: Best Practices
Visibility over your organization's IT assets is essential for a strong security posture and proactive IT operations. An asset is any component that contributes to delivering a service managed by IT. Examples of IT assets include physical devices like laptops, printers, or network switches and virtual assets such as software or cloud resources.
ITSM (Information Technology Service Management) asset management provides a structured approach to identifying, tracking, and maintaining assets throughout their lifecycle. The ITSM asset management practice ensures compliance with policies and regulations while delivering critical data for informed decision-making.
While not a strict prerequisite, a robust asset management program can facilitate the adoption of more sophisticated ITSM practices, such as implementing a configuration management database (CMDB) to map IT infrastructure relationships or establishing an endpoint detection and management (EDM) system to manage and secure end-user devices.
In this article, we will explore the key components of ITSM asset management, focusing on benefits and best practices.
ITSM asset management best practices
The table below details five critical ITSM asset management best practices that this article will explore in more detail.
Best practices | Description |
|---|---|
Define an asset management policy | Create an asset management policy that includes a clear definition of what constitutes an asset within your organization, how assets are categorized and what data needs to be captured for each category |
Create a complete inventory of your assets | Identify available resources to obtain a snapshot of your current assets |
Define a lifecycle management plan to maintain an accurate inventory | Identify the activities that affect how your assets are updated and maintained |
Build reports to track changes affecting your assets and inventory | Create metrics, dashboards, and KPIs that accurately reflect your inventory count, usage, and compliance, as well as reflect the success of your process and provide financial data to other departments |
Provide training and visibility of the asset management process | Clearly present the importance of asset management as a key component of ITSM |
What is ITSM asset management?
An IT asset is any component that contributes to the delivery of IT services or supports business operations within your organization. Typically, an IT asset can be defined as any hardware, software, data, cloud resource, or IT infrastructure component that has:
- a value exceeding a certain amount,
- is owned or leased by your organization,
- and/or is used to support business operations or deliver certain IT services.
An IT asset management (ITAM) practice follows a systematic approach to managing your IT assets throughout their lifecycle. The primary goal of ITAM is to ensure efficient utilization of IT assets, optimize performance, and maintain compliance with industry standards. A strong asset management strategy also eventually makes it easier to track software licenses and warranties so you can avoid unnecessary compliance penalties or renewals.
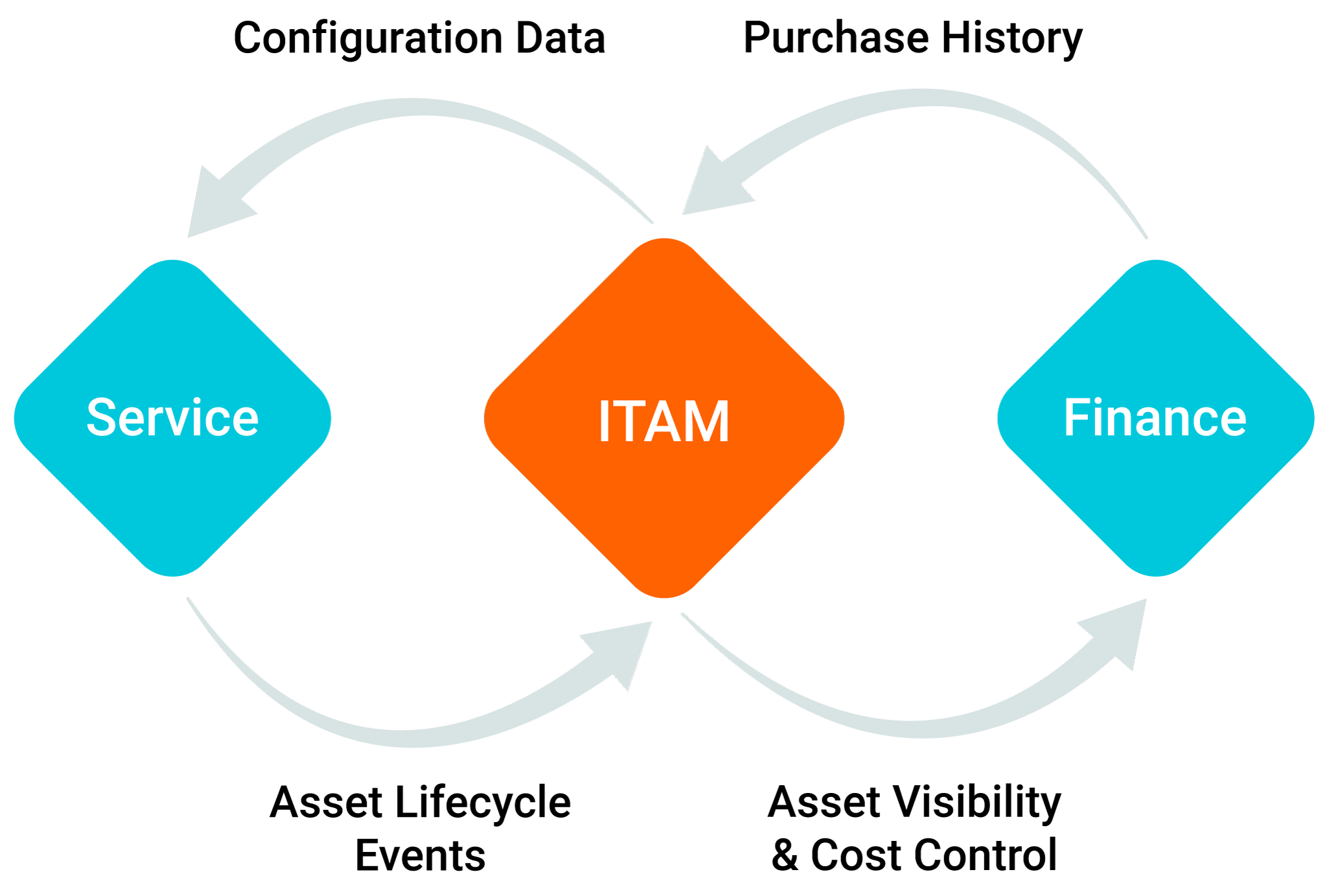
ITAM as a single source of truth for hardware, software, and users ()
Learn :
- Track your organization’s hardware and software inventory, including computers, servers, laptops, mobile devices, networking equipment, and virtually any other tech asset.
- Track and tag hundreds of hardware properties, software titles, and user and location history from your Windows, iOS, and Chrome OS devices.

Transform Asset Data Into Asset Clarity
From hardware to software, gain visibility and control over your IT environment. Optimize asset utilization and help reduce costs directly within Service Desk.
Getting started with ITSM asset management
The first step in implementing an ITAM practice is defining a clear policy as the roadmap for implementation. This means identifying your IT assets, understanding what data you need to collect, and determining how it will be used. It is worth noting that IT assets come in many forms and are used in many ways, often by departments beyond IT.
Categorize asset types
ITIL, a best-practice framework for IT service management, defines an asset as any item of value that supports the delivery of a service. IT assets can be categorized into two primary categories:
- Hardware assets involve anything you can physically touch. These include physical items such as laptops, desktops, servers, physical network devices (switches, routers), printers, and mobile devices like phones and tablets.
- Software assets include software packages, licenses, operating systems, virtual machines, and middleware.
Additional IT asset examples
For specific use cases, organizations can further sub-classify assets into categories such as:
- Data assets: Data backups, repositories, databases.
- Documentation assets: Standard operating procedures (SOPs), knowledge bases, intellectual property.
- Facility assets: HVAC systems, data center infrastructure, power supply systems.
- Security assets: Encryption keys, authentication tokens, and security policies.
Determining the relevant data
Once asset types are identified, the next step is to determine the data required to manage those assets effectively. In most cases, when data is collected with clear objectives in mind, it’s easier to analyze and extract valuable insights.
Three key domains play a vital role in this process:
- Asset management focuses on the financial and contractual aspects of assets. It encompasses the processes of procurement, deployment, maintenance, and disposal, ensuring compliance with licensing agreements and regulatory requirements. Key data points for asset management include:
- Purchase date and cost
- Warranty information
- License details (expiration dates, number of users)
- Maintenance contracts
- Configuration management database (CMDB) is the centralized repository of technical information about all configuration items (CIs) within the IT environment. Capturing relationships and dependencies between CIs helps facilitate better change management, incident response, and overall IT service delivery. Relevant data points within a CMDB might include:
- Hardware specifications (CPU, memory, storage)
- Software versions and configurations
- Network connections and dependencies
- Relationships to other CIs
- Endpoint device management (EDM) refers to a subset of overall IT asset management that focuses specifically on managing end-user devices and ensuring these devices are secure, compliant, and properly configured. Key data in this domain includes:
- Device type and model
- Operating system and version
- Security software status
- User assignment and location
For ITSM asset management, organizations must determine which attributes are required to manage utilization and compliance. Capturing attributes related to purchase price, maintenance costs, and depreciation can also help calculate each asset's total cost of ownership (TCO).
The table below lists some commonly used asset management attributes.
Attribute | Utilization | Costs | Compliance |
|---|---|---|---|
Asset ID | Custom-assigned identifier that uniquely identifies each asset within your organization | Helps avoid duplicate purchases and ensures accurate cost allocation | Essential for internal audits and reporting |
Asset type | Identifies asset categories for proper resource allocation | Assists in budgeting according to different asset types | Ensures accurate management of compliance requirements by asset type |
Unique identifier (e.g., Serial number, MAC address) | Standardized identifier to distinguish an asset based on manufacturer information or specific device properties | Avoids duplicate purchases, improving budgeting | Necessary for audits and tracking in compliance with regulations |
Description | Defines an asset’s purpose for proper deployment | Determines an asset's importance in cost planning | Ensures appropriate classification for regulatory adherence |
Owner | Assigns responsibility for determining how an asset is utilized | Ensures accountability for cost control | Ensures asset owner is aware of compliance responsibilities |
Purchase date | Helps determine an asset's operational lifecycle | Provides data for budgeting and cost analysis | Records for financial and compliance audits |
Deployment date | Tracks an asset’s active use period | Helps evaluate ROI and depreciation start | Relevant for compliance reporting of active assets |
Retirement date | Assists in managing asset lifecycle planning | Helps forecast replacement costs | Ensures timely retirement to meet compliance standards |
Purchase Cost | Assists in cost-benefit analysis of asset usage | Directly impacts budget and expense tracking | Records for audit compliance and financial regulations |
Depreciation method | Indicates usage over time | Impacts financial reporting and tax purposes | Important for compliance with financial regulations |
Current value | Assesses today’s worth | Impacts decisions on asset replacement or retention | Important for audit tracking and financial reporting compliance |
License information | Ensures software is properly deployed and tracked | Helps avoid penalties by managing renewal costs | Critical for maintaining software compliance and avoiding penalties |
Create a complete inventory of your assets
Identifying asset attributes and discovering existing resources often occur in tandem. A common practice is to simultaneously determine the key data points needed for each asset type and employ various methods to locate and identify all available IT assets.
Asset discovery and identification involves a series of steps:
- Utilizing practices to locate assets (network scanning, agent-based discovery, manual audits).
- Collecting relevant attributes for each asset based on the defined attributes.
- Reconciling data from multiple sources to create a single, unified view of all IT assets.
Manual inventories offer great flexibility for customization and can be very thorough when executed properly. However, it is also time-consuming and can be prone to errors, stale data, and incomplete information.
Asset discovery tools help automate the process and provide real-time updates. A discovery tool can also map virtualized and cloud resources that are otherwise difficult to manifest through a manual process. However, there are several trade offs to consider when using discovery tools. Some of them can be expensive and complex. There is also a perceived tendency to gradually rely too much on automation and skip key manual review steps.
Choosing between manual asset inventory and discovery tools should depend on your organization’s specific needs, resources, and environment. A manual inventory is considered best for small organizations with only a couple of dozen assets or unique requirements. However, mid-to-large scale enterprises or those with diverse IT environments usually benefit from the efficiency and comprehensiveness of automated discovery tools. In some cases, a hybrid approach that combines both methods may provide the best results.
Define a lifecycle management plan to maintain an accurate inventory
Every IT asset goes through different stages–a lifecycle starts with its acquisition and ends with its retirement. Asset lifecycle management is the process of overseeing and managing the entire lifecycle, ensuring assets are effectively utilized, costs are controlled, compliance is maintained, and value is maximized.
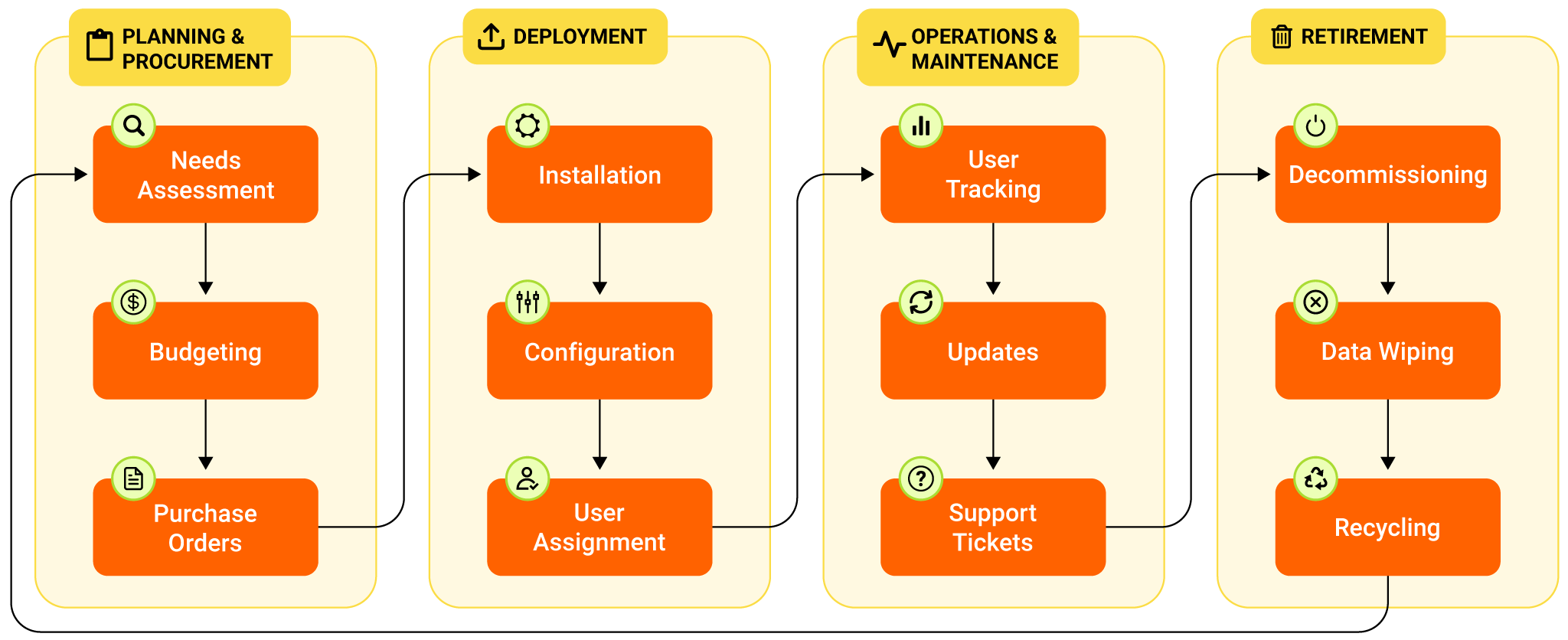
Stage of an asset lifecycle
Instead of being a standalone process, a typical asset lifecycle management leverages inputs from other ITIL practices to update and maintain each asset. The following examples highlight a few of the key processes involved and how these, along with other processes and inputs, ensure an asset is managed throughout its lifecycle:
- Procurement manages how assets are acquired and sets the stage for its lifecycle
- Vendor management influences asset support and administers timely replacements
- Change management minimizes asset disruptions
- Release management ensures the smooth deployment of new assets and software versions to production
Set up reporting and monitoring metrics
Experienced ITAM professionals use reporting as a strategic tool to showcase the value of their ITAM's practice. Instead of just looking at the initial worth of an asset, they can dig deeper to figure out the total cost over its entire lifespan. This means factoring in things like maintenance, support, and even how much it will cost to dispose of it properly.
It's also important to show how ITAM saves money or makes the company more efficient. Track how much you’ve saved by optimizing software licenses, how much downtime you've avoided by being proactive with maintenance, and how much more efficient your processes have become through automation. Some tools also offer predictive modeling to anticipate things like when an asset might break down, when the software might have security issues, or when licenses are about to expire.
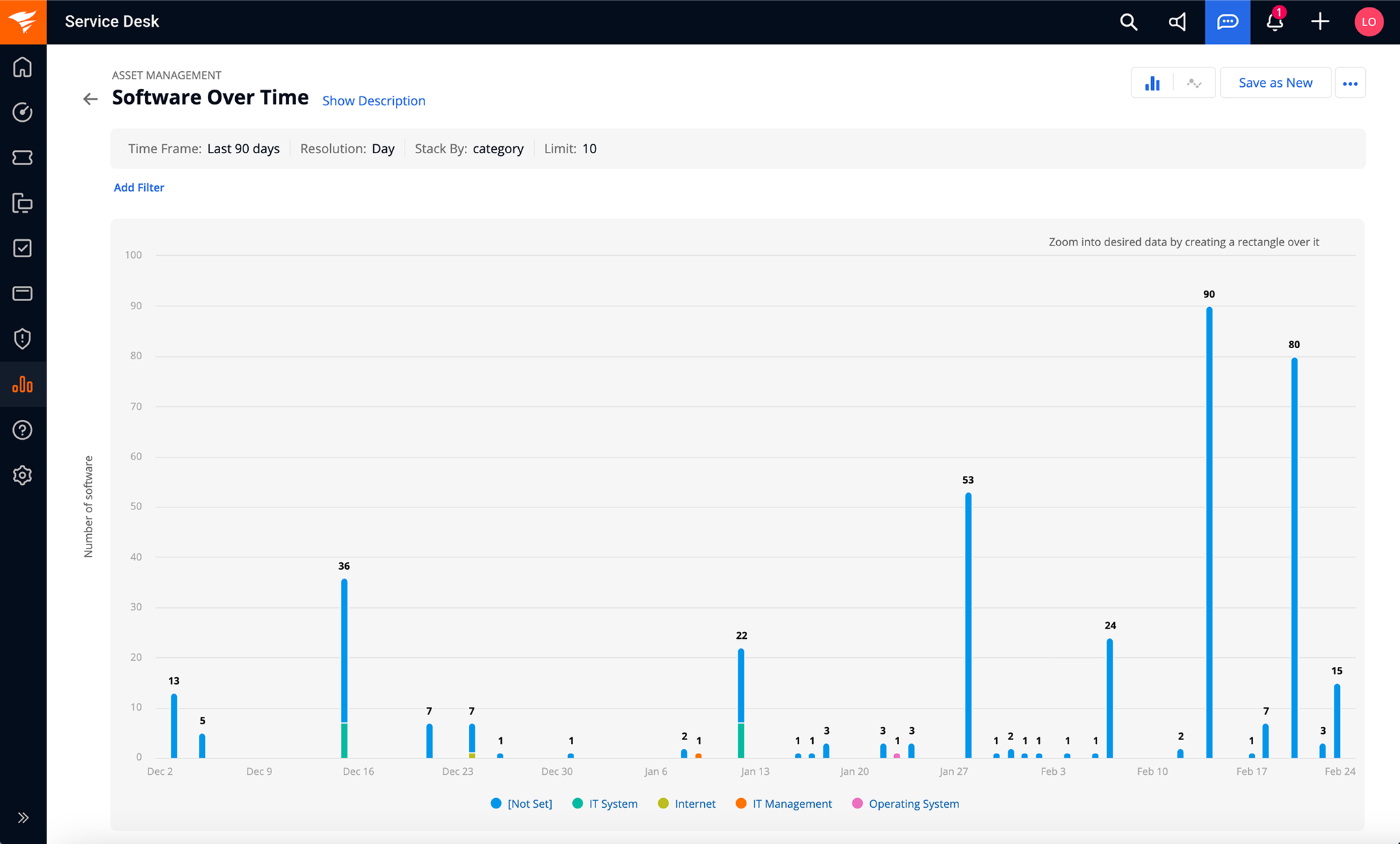
SolarWinds ITAM Asset Management Reporting
Metrics and reports also provide a baseline for continuous improvement and insights into compliance, accuracy, and overall process success, aiding in budget and roadmap planning.
Consider the following when establishing a reporting and metrics framework for your ITAM practice:
- Assign roles and responsibilities: You will need to know who is responsible for monitoring the data, generating reports, and suggesting appropriate actions based on results.
- Define objectives and KPIs: Choose the key performance indicators (KPIs) that align with business goals and ITAM objectives.
- Select monitoring tools: Several tools help organizations track asset performance, usage, and compliance. Choosing the right tool can make this task easier and give you the best results.
- Decide how to collect your data: Automation is the key here. Tooling should automatically collect data on new tasks like new software installation, license usage, and hardware lifecycle stages. Set up automated processes to collect data on assets, such as software installations, hardware lifecycles, and license usage.
- Create standards for your reporting: How do you want to present your data to your stakeholders? Each stakeholder may require different formats. You must understand what is needed and define that format so the information presented is clear and actionable to your audience.
- Schedule a regular cadence for reports: Whether reporting is provided daily, weekly, or monthly is based on business needs and the relevancy of the data.
- Look for continuous improvement: Regularly reviewing reports and the data presented in them allows you to identify trends, look for gaps, and keep your ITAM process updated.
Provide training and visibility
After setting up the initial aspects of ITAM, ensure people know about your processes and more importantly, understand how to use it. A good training plan should provide increased visibility across all IT and their stakeholders. When people understand the benefits and functionalities of the ITAM system, they are more likely to use it effectively and contribute to its success. Appropriate training also ensures that everyone involved in ITAM processes understands how to collect, input, and maintain accurate data, which is eventually fundamental for reliable reporting and informed decision-making.
Consider the following when training users about your ITAM practice:
- Start with a comprehensive training outline: In your training, outline important topics such as the advantages of the ITAM process, ITAM’s role within the company, and increased efficiency and compliance.
- Describe the key benefits of ITAM: Discuss subjects like cost savings, increased control, improved productivity through automation, and the ability to make better decisions based on better data.
- Focus your training on the correct audience: Staff of different verticals may have different needs than your business stakeholders. Ensure your training shows how ITAM influences each appropriately.
- Provide regular updates and continuous training: Schedule periodic sessions for discussions, feedback, and learning opportunities to show people that ITAM is an ongoing process and important to their work environment.
Assess your ITAM strategy with the SolarWinds Maturity Model
Establishing a quality ITSM asset management plan takes significant planning and effort. If rightly implemented, the results are worth it. As a starting point though, it is important to assess the return on investment (ROI) for IT services.
Do your services support digital transformation, fuel business growth, and mitigate risks? And crucially, do the services help achieve the goals at an acceptable total cost of ownership?
There are smarter ways to achieve IT excellence, and a top-notch ITAM setup doesn’t have to break the bank.
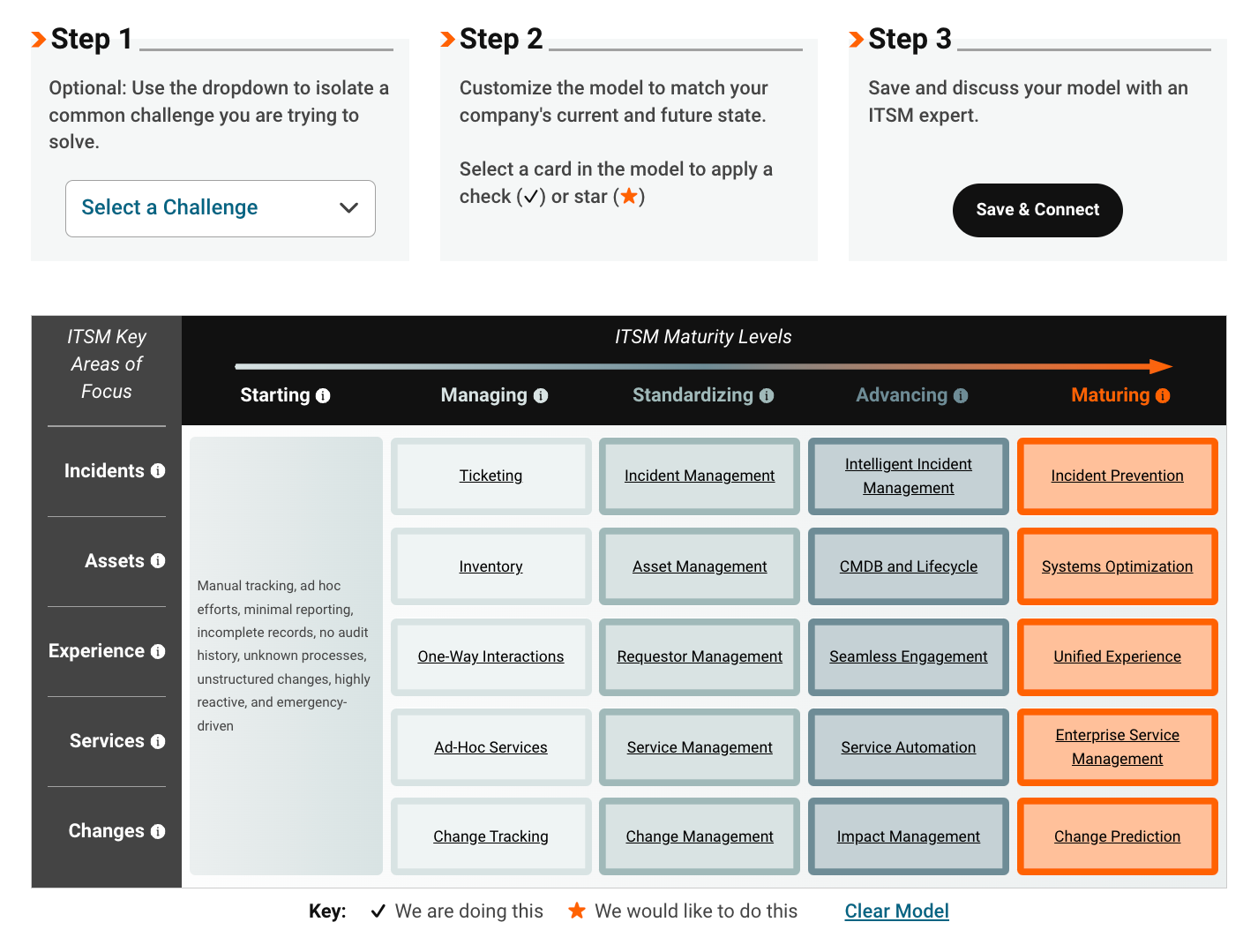
Whether you're a small startup or a large corporation, SolarWinds’ ITSM Maturity framework can help you navigate the complexities of IT asset management. This free tool can act as a guide, helping you understand your current ITAM maturity, define your desired outcomes, and determine the tools you need to get there.
Explore our interactive ITSM maturity model here.
Ready to create ITSMagic for your organization?