SSH Terrapin Prefix Truncation Weakness
(CVE-2023-48795)
Summary
The SolarWinds Information Security team has been made aware of CVE-2023-48795, a vulnerability concerning OpenSSH, an open source implementation of the SSH protocol, which enables attacker to downgrade authentication and effectively crack the password.
What happened?
A vulnerability was reported in the OpenSSH third party library. Exploiting SSH Terrapin allows a man-in-the-middle attacker to truncate important parts of the SSH handshake, without closing the SSH connection, which creates a security impact for the SSH client/server.
Have there been any reports?
We have not received any reports from our customers of attacks related to this vulnerability.
How is SolarWinds addressing this?
For Security Event Manager (SEM), a fix is already in the works to prevent the issue from occurring and we recommend upgrading to the fix version once released.
For SolarWinds SCP, a workaround will be provided to disable the vulnerable ChaCha20-Poly1305 cipher in the OpenSSH client and server configurations.
What actions should I take?
For Security Event Manager (SEM), a fix is already in the works to prevent the issue from occurring and we recommend upgrading to the fix version once released.
For SolarWinds SCP, Customers can follow the steps below to disable the vulnerable ChaCha20-Poly1305 cipher
- Go to this folder C:\Program Files (x86)\SolarWinds\SFTP & SCP Server and open the file SolarWindsSftpServer.exe.config with a text editor
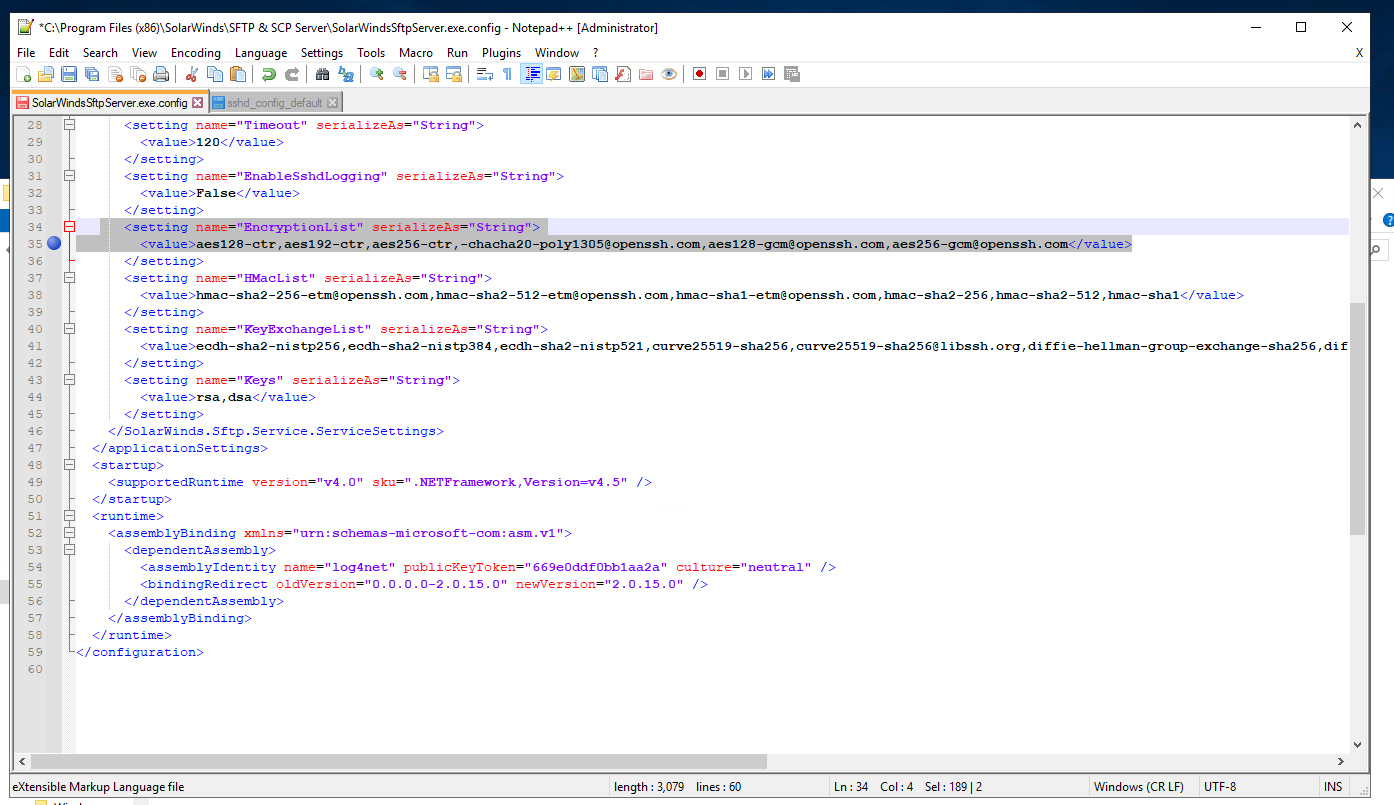
- Open the file with put a dash before the chacha20 in the highlighted line (Already done in this screenshot)
- Restart the Solarwinds SCP/SFTP Service
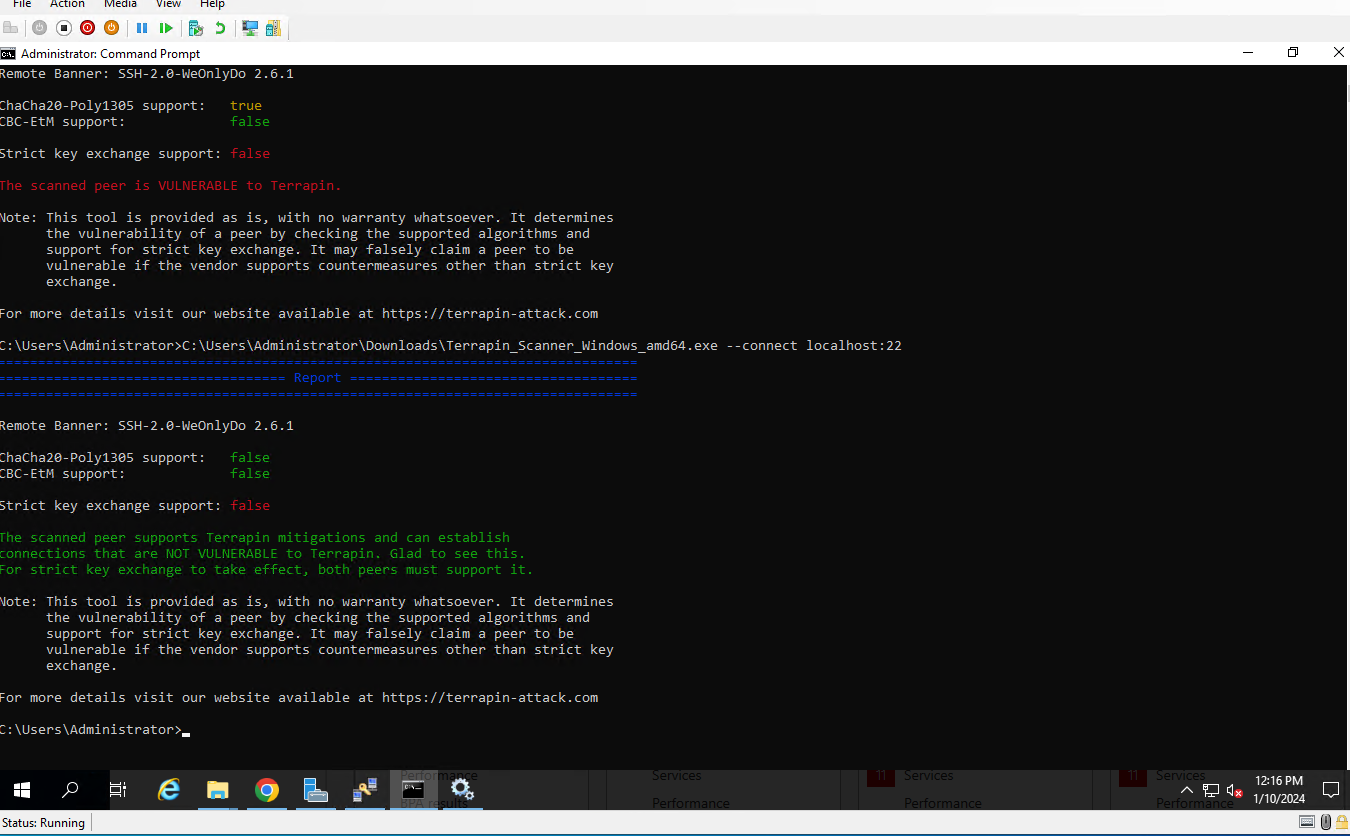
- The top run of the scanner was before the above changes and the second run is after.
Affected Products
- SEM 2023.4 and previous versions
- Solarwinds SCP
Advisory Details
Severity
5.9 Medium