Elevating IT Service Delivery with ITSM Best Practices
Fix bugs, respond to tickets, and put out fires as they arise—that’s often what we think of when we picture IT in action. But there’s a bigger picture to consider: how do organizations ensure services are designed well, delivered efficiently, and constantly improved?
IT Service Management (ITSM) is the broader framework that oversees the entire service lifecycle, from creation to operation and finally to retirement. If you’re new to ITSM or just looking to improve your approach, adopting an ITSM tool is a great starting point. But a tool, after all, is just a tool.
To truly transform your IT service delivery, you need a holistic approach that combines the right technology with a commitment to ITIL best practices. Your chosen ITSM tool should be built on the ITIL framework and delivered out-of-the-box with full ITIL support.
In this article, we discuss the key ITSM practices and considerations to help you assess your organization's current maturity level and chart a course for continuous improvement.
Summary of ITSM Best Practices and Considerations
ITSM practice | Considerations |
|---|---|
Incident management | Prioritize and resolve incidents efficiently using tiered support, automation, and clear runbooks. Monitor for trends and proactively address recurring issues. |
Service desk and request fulfillment | Act as the central point of contact for users, providing efficient support and fulfilling service requests. Adopt automation, self-service, and proactive engagement to enhance user experience and streamline operations. |
Problem management | Proactively identify and address root causes of incidents to prevent recurrence. Utilize trend analysis, root cause analysis techniques, and collaboration across teams to achieve lasting solutions. |
Change management | Establish a formal change management process with a centralized change catalog. Automate workflows and implement change conflict prevention to ensure smooth transitions and minimize disruptions. |
IT asset management (ITAM) | Implement a comprehensive ITAM strategy to track and manage IT assets throughout their lifecycle. Ensure accurate asset data, monitor utilization, and integrate with other ITSM processes for optimal value and compliance. |
Knowledge management | Centralize and share knowledge effectively through a user-friendly knowledge base. Encourage contributions, gather feedback, and leverage AI to empower users and improve service quality. |
Service delivery | Define clear Service Level Agreements (SLAs) for all IT services and continuously monitor performance against them. Configure automated escalations and notifications to ensure timely intervention and prevent SLA breaches. |
Key Components of ITSM
ITIL v3 organized processes around five service lifecycle stages—strategy, design, transition, operation, and continual service improvement. ITIL 4 focuses on the same service principles but subtly emphasizes a broader Service Value System (SVS) and a more flexible Service Value Chain (SVC). It is more adaptable to the specific context and organization requirements. Significantly, these service stages aren’t limited to just IT. They are flexible and often valuable for managing any enterprise service operation, from customer support to HR onboarding.
IT Service Management (ITSM) has evolved over time, with ITIL providing a popular framework for its implementation. Earlier versions of ITIL, such as ITIL v3, emphasized a five-stage lifecycle approach, as highlighted in the table below.
Stage | Focus | Key activities |
|---|---|---|
Service strategy | Aligning IT services with business needs | Defining service portfolios, establishing SLAs, financial management |
Service design | Creating and developing new or changed service blueprints | Service catalog design, capacity planning, risk management |
Service transition | Building and deploying new or changed services into the live environment | Change management, release management, knowledge transfer |
Service operation/delivery | Ensuring efficient delivery of services and day-to-day operations | Incident management, problem management, request fulfillment |
Continual Service Improvement (CSI) | Continuously improving the effectiveness and efficiency of processes and services | Performance analysis, process optimization, feedback loops |
Core ITSM service stages and purpose
Within IT, these five core stages work in sync to form the ITSM lifecycle, ensuring that IT services are planned, designed, transitioned, operated, and continually improved to deliver maximum value to the business.
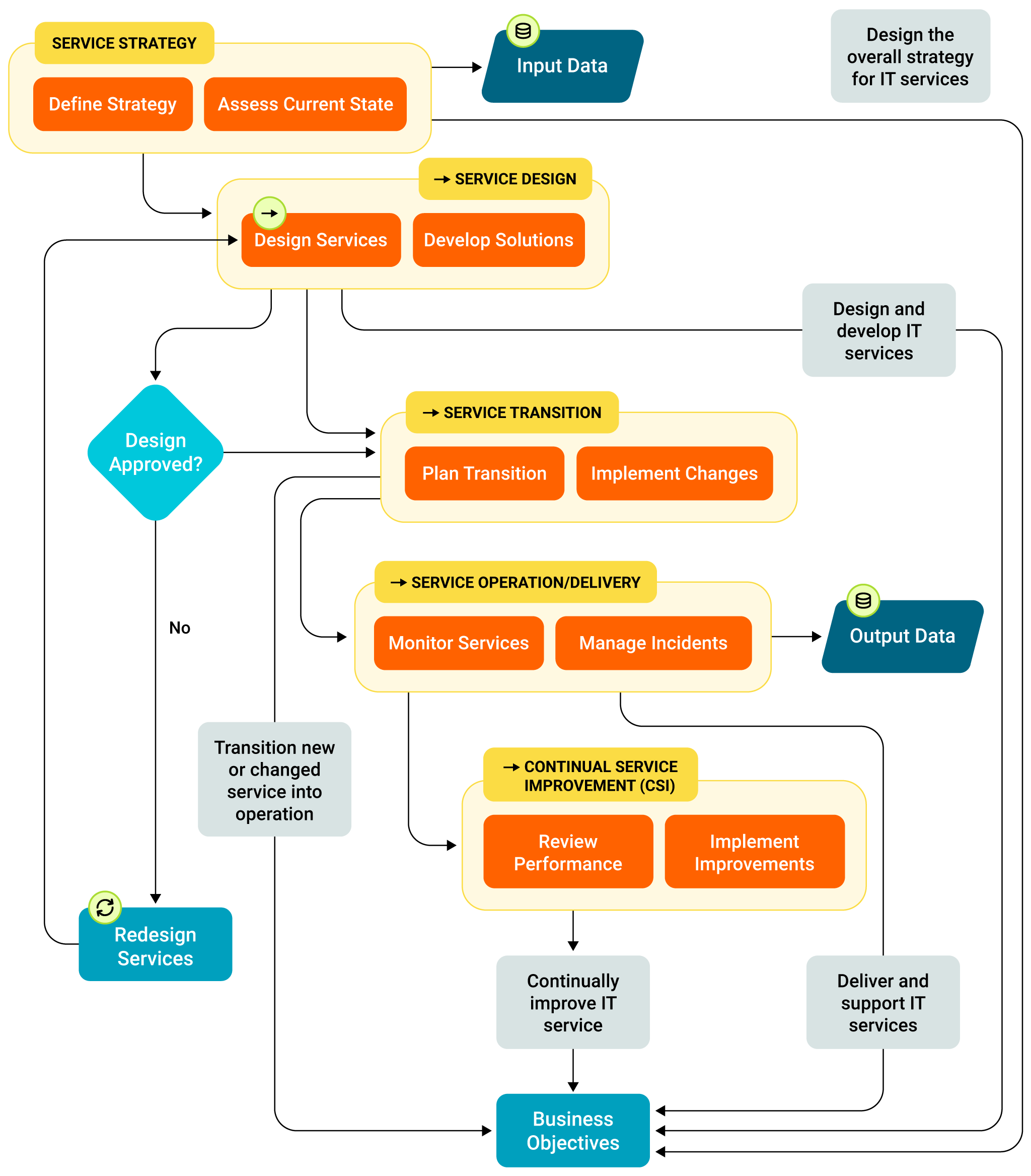
Service lifecycle flowchart
ITIL 4 has shifted to a more holistic and integrated approach. Instead of distinct stages, ITIL 4 emphasizes these activities' interconnectedness within the context of the Service Value System (SVS). This system considers four critical dimensions for value creation: organizations and people, information and technology, partners and suppliers, and value streams and processes.
While the key activities from the previous stages are still relevant in ITIL 4, they are now viewed through the lens of these four dimensions and integrated into various practices within the SVS.
ITSM Practices and Considerations
ITSM envisions IT as a service beyond the technical aspects of software. The ITSM framework outlines how IT teams can ensure users receive reliable, efficient, and constantly improving IT services.
Key ITSM practices and considerations are given below.
Incident Management
Incident management restores normal service operations after an incident to minimize business impact and strengthen an organization’s resilience. However, the practice may not always solve the problem (and the underlying root cause) completely. Rather, the approach focuses on implementing temporary workarounds or quick fixes to handle sudden disruptions and achieve normalcy as soon as possible.
A multi-tiered support system with skill-based routing allows more complicated incidents to be transferred to experts. Incidents handled by the right experts improve first-call resolution (FCR) rates and reduce escalation.
Organizations create standardized runbooks to guide technicians through common incident resolution steps. These guides include decision points so technicians can adapt to different situations.
It is important to note that a key part of the process is to:
- Collect critical information about the incident
- Identify its potential causes, and
- Document the steps taken to resolve it.
The information is then passed to problem management teams for a deeper investigation and a permanent solution that prevents similar incidents from happening again.
Recommendations
- Implement AI-powered assistance to triage and assign incidents swiftly.
- Connect your runbooks with automation tools so they can take action automatically when needed.
- Set up automated incident creation when monitoring systems detect anomalies or predefined thresholds are breached. A proactive approach minimizes downtime and allows you to tackle issues before they escalate into major disruptions.
- Track key metrics like MTTR (mean time to resolve), incident volume, and customer satisfaction to assess the effectiveness of your efforts and opportunities to optimize your incident management strategy.
- Ensure that incident management processes are tightly integrated with the CMDB for accurate impact assessment, identification of affected services, and facilitating root cause analysis.
Simpler Service Management Starts Here
Ready to put these best practices into action? Service Desk provides you with the tools to manage changes, resolve incidents, and gain control over your IT.
Service Desk and Request Fulfillment
A service desk is the dedicated point of contact between users and IT. It’s where incidents are reported, questions are answered, and new service requests are initiated. The request fulfillment process includes everything from request receipt to completion, including tasks like approvals, resource allocation, and tracking progress.
A typical service request flow is as follows:
- A user submits a request, often through a self-service portal or by contacting the service desk directly.
- The service desk categorizes the request, assesses its impact, and determines the appropriate applicable SLOs.
- Based on the request type and SLOs, the service desk may seek approvals and assign the request to the relevant team or individual.
- The assigned team works to fulfill the request, keeping track of progress and ensuring that SLOs are met.
- Once the request is completed, the service desk closes the ticket and communicates the outcome to the user.
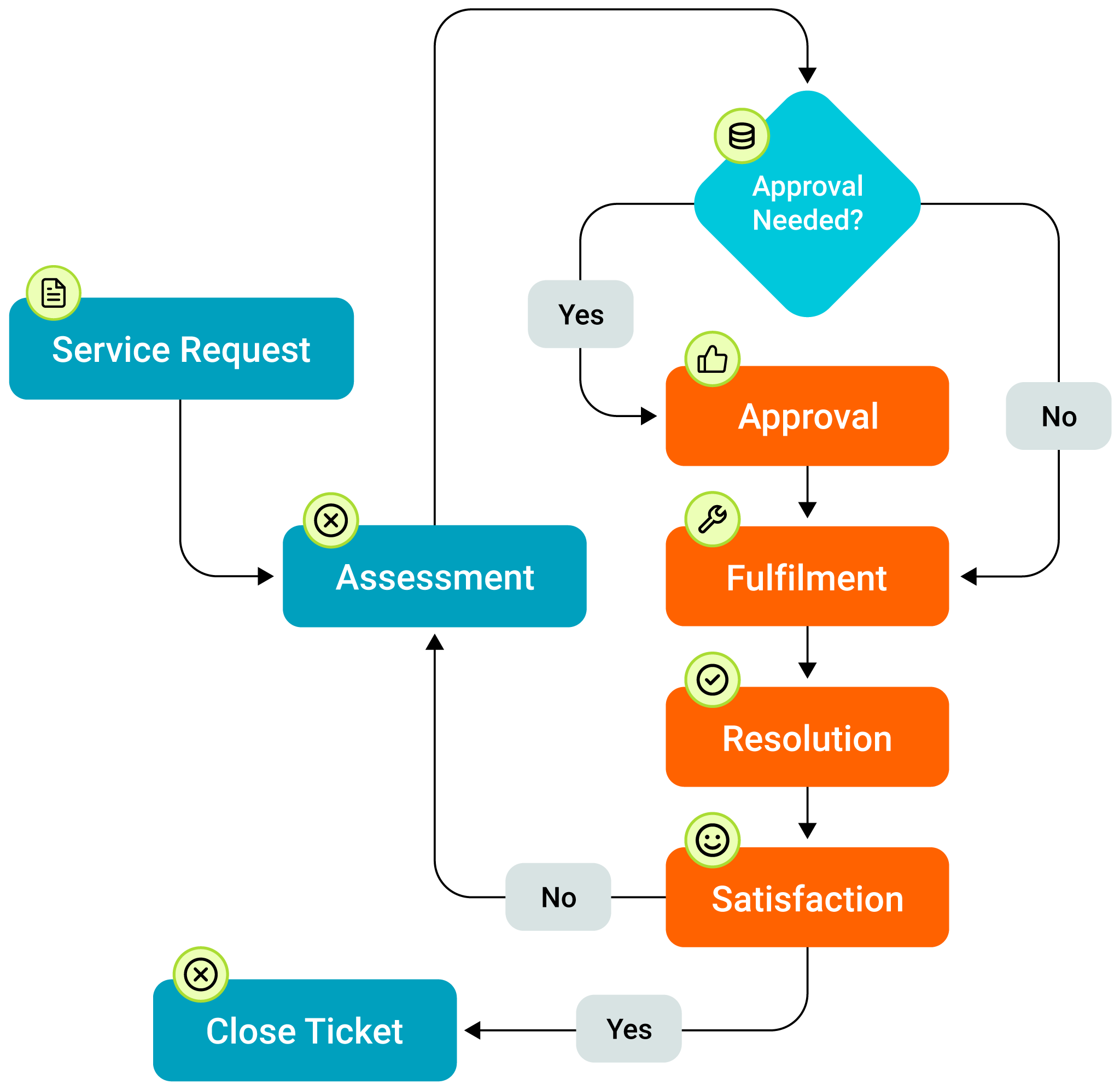
Service request fulfillment flow
Recommendations
- Implement request workflow automation to reduce manual effort, minimize errors, and accelerate service delivery.
- Extend self-service capabilities beyond basic requests. Users should be able to initiate more complex workflows, such as new employee onboarding or cloud resource provisioning, through intuitive self-service portals.
- Refine your service catalog to ensure it is user-friendly and up-to-date. Consider implementing a tiered catalog structure to cater to different user groups and their specific needs.
Problem Management
A problem in ITSM is the root cause behind one or more incidents exhibiting similar characteristics. Detecting problems is sometimes straightforward, such as when multiple incidents affect the same service or a workaround proves elusive. However, other times, it demands a more in-depth analysis of your IT infrastructure.
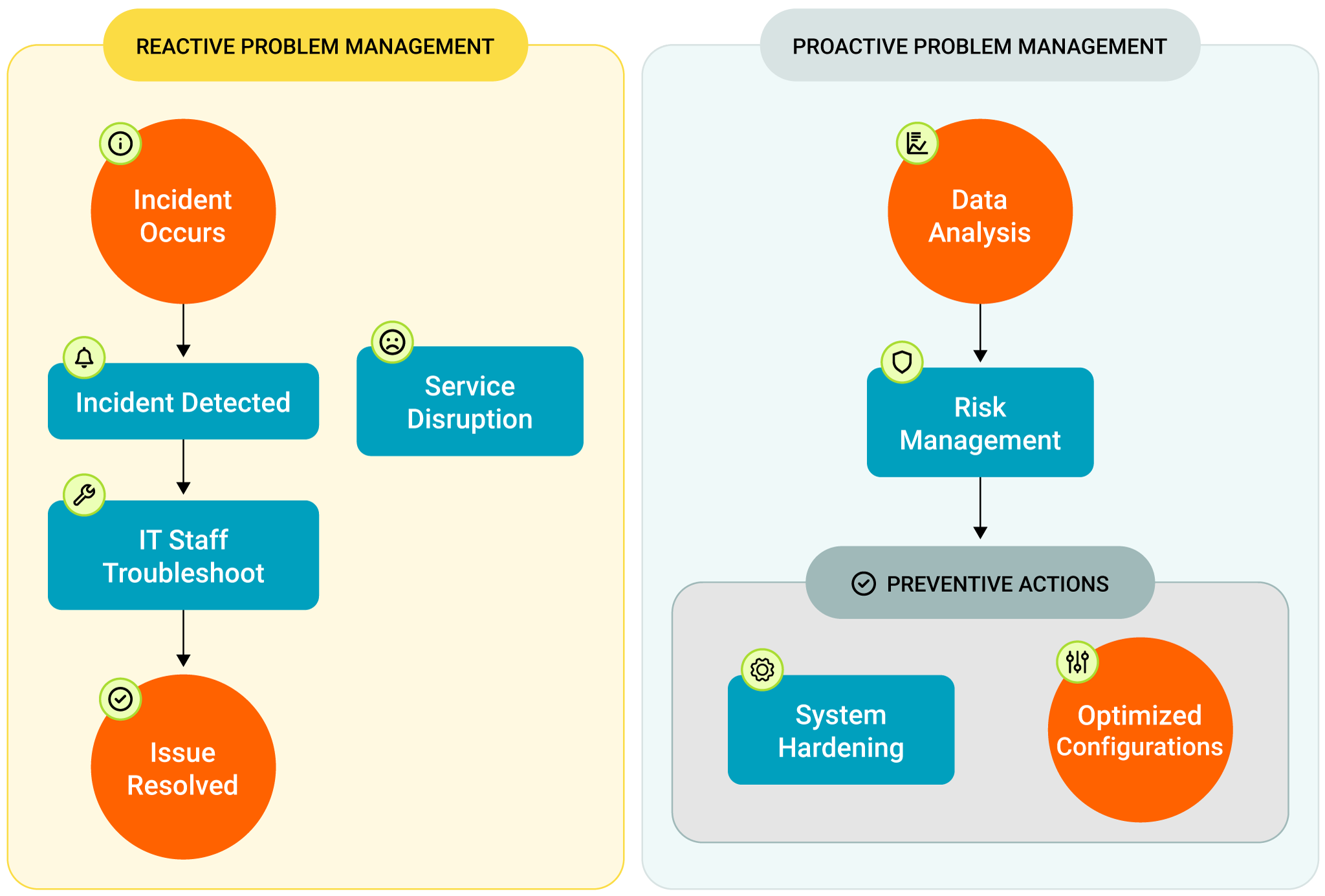
Reactive vs Proactive Problem Management
A typical practice to uncover the true root cause of a problem is to go beyond superficial fixes and employ structured root cause analysis (RCA) techniques. One way to do this is by using the “5 Whys” method, where you keep asking ‘why’ until you get to the bottom of the issue. Another option is to utilize an Ishikawa or Cause-and-Effect diagram that visually maps out potential causes, categorizing them into areas like people, processes, technology, and environment.
Once you’ve identified a problem’s root cause, the goal must be to prevent it from happening again. Implement proactive measures like system hardening, configuration changes, or even software updates to reduce the likelihood of recurring incidents.
Recommendations
- Implement a risk-based prioritization model that considers the impact of each problem on business operations, its severity, and its occurrence frequency. You can then focus your resources on addressing the most critical issues and prevent them from escalating into major incidents.
- Document every problem, its root cause, and the solution implemented. A knowledge base is a valuable asset for your IT team that enables faster resolution of similar incidents in the future.
- Use a known error database for trend analysis, predictive modeling, and other proactive problem-prevention strategies.
Change Management
Change management implements a series of checkpoints to ensure any IT change is thoroughly evaluated, authorized, and planned before implementation. It reduces the likelihood of unexpected incidents. Typically, the change management process contains five stages:
- Change request
- Change assessment and planning
- Change approval
- Change implementation
- Change impact review.
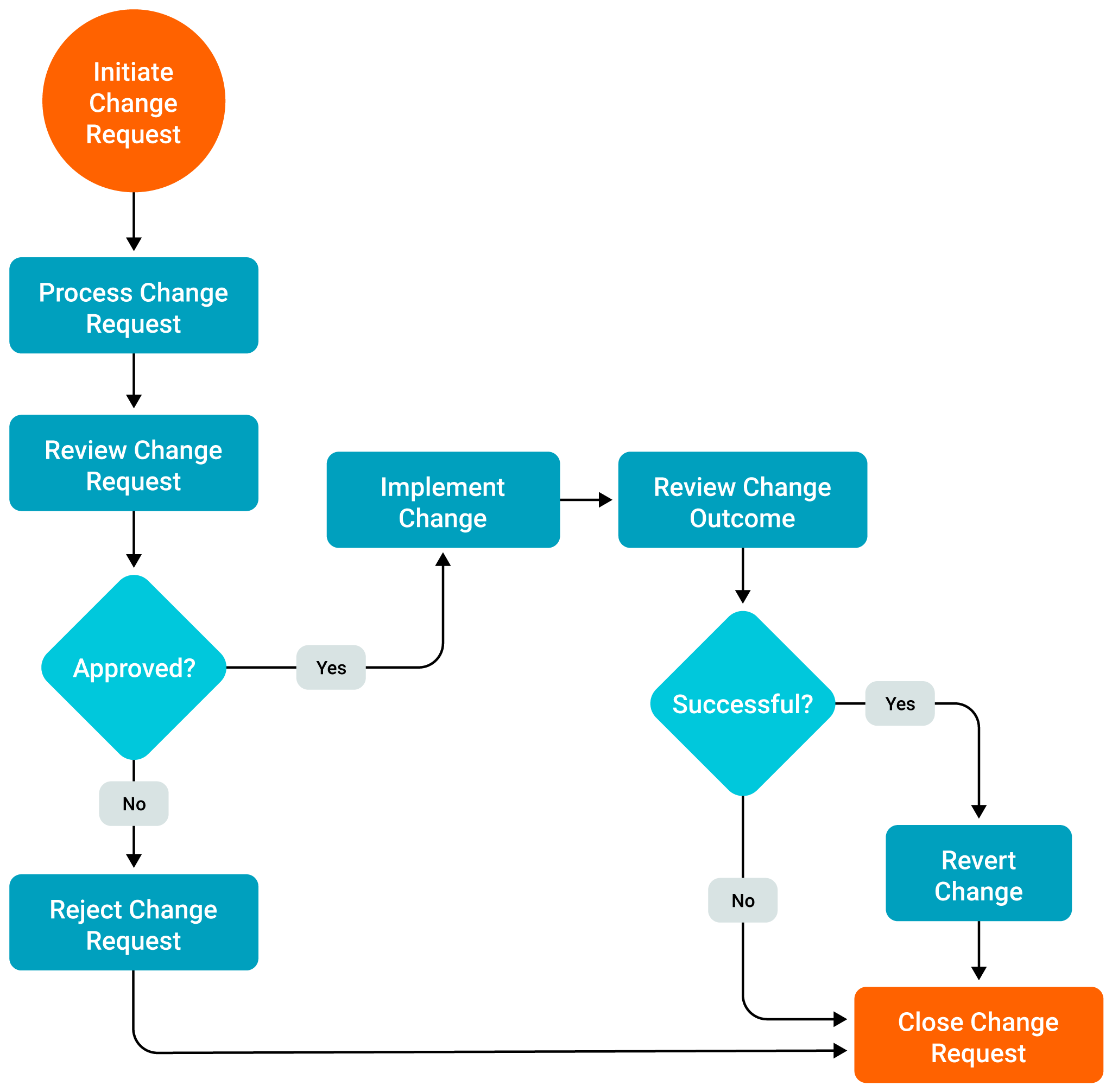
A typical change request flow
Recommendations
IT changes must demonstrably enhance functionality and services to achieve organizational goals. While IT governance ensures this alignment, smaller organizations might lack formal structures. In such cases, the change management team must take ownership and ensure IT changes actively contribute to organizational success.
Many changes, particularly those involving IT, have subtle or indirect impacts that can be difficult for stakeholders to grasp. All changes should be formally requested, documented, and tracked through a centralized change catalog to prevent unplanned and potentially disruptive IT alterations.
Use automation to spot potential clashes between changes and automatically adjust schedules if needed. Go beyond just looking for overlapping times; also check how different systems and parts of your IT setup rely on each other.
Implement automated workflows to trigger rescheduling or other mitigation actions. The practice speeds up the change process and minimizes human error risk.
Asset Management
An asset register is a key governance tool containing information on asset status, ownership, and other attributes. It helps manage your IT assets from the moment you think about buying them to the day you get rid of them. A lifecycle approach is applicable to all IT assets, regardless of whether they’re on-premises or cloud-based. Organizations with a SaaS-heavy environment need a CMDB (Configuration Management Database) to map cloud assets and gain visibility into related services, costs, risks, and compliance.
Since IT asset management (ITAM) serves as the foundation for planning and decision-making across various IT operations, it must be integrated with other core ITSM practices.
Domain | How IT asset lifecycle data informs and supports |
|---|---|
Incident management | Aids in troubleshooting and resolving outages and performance issues related to IT assets. |
Service request management | Facilitates fulfillment of user requests for IT asset allocation, changes, and removal. |
Change management | Provides crucial information for assessing, authorizing, and scheduling changes to IT assets. |
Service configuration management | Transforms IT assets into trackable configuration items to manage their attributes and relationships within the broader IT environment. |
Information security management | Enables risk assessment and implementation of controls to protect IT assets from vulnerabilities. |
Service financial management | Provides essential data for budgeting, accounting, and tracking the financial status of IT assets. Ensures alignment with enterprise financial policies. |
Recommendations
- Proactively verify and audit your asset register to ensure it reflects reality. While automation helps, a human touch is still important to catch any anomalies. Verification should be ongoing to uncover gaps and ensure accuracy. On the other hand, audits should be planned and involve external parties to meet governance and compliance needs.
- An automated system is preferred for organizations managing over a dozen IT assets. Automated systems bring standardization, automated discovery, label generation, relationship mapping, and seamless data exchange with other systems.
- Customize your Software Asset Management (SAM) practices to accommodate the complexities of software licensing, deployment models, and usage patterns to support a cloud-centric model. Software assets require a distinct management approach compared to hardware, as software value fluctuates based on usage.
Knowledge Management
A community-driven, open knowledge-sharing platform helps everyone in your company, whether they’re creating products or providing services. The knowledge management practice utilizes a knowledge base as a self-service repository of information regarding products, services, departments, or specific topics. It can contain FAQs, troubleshooting guides, or any other essential information.
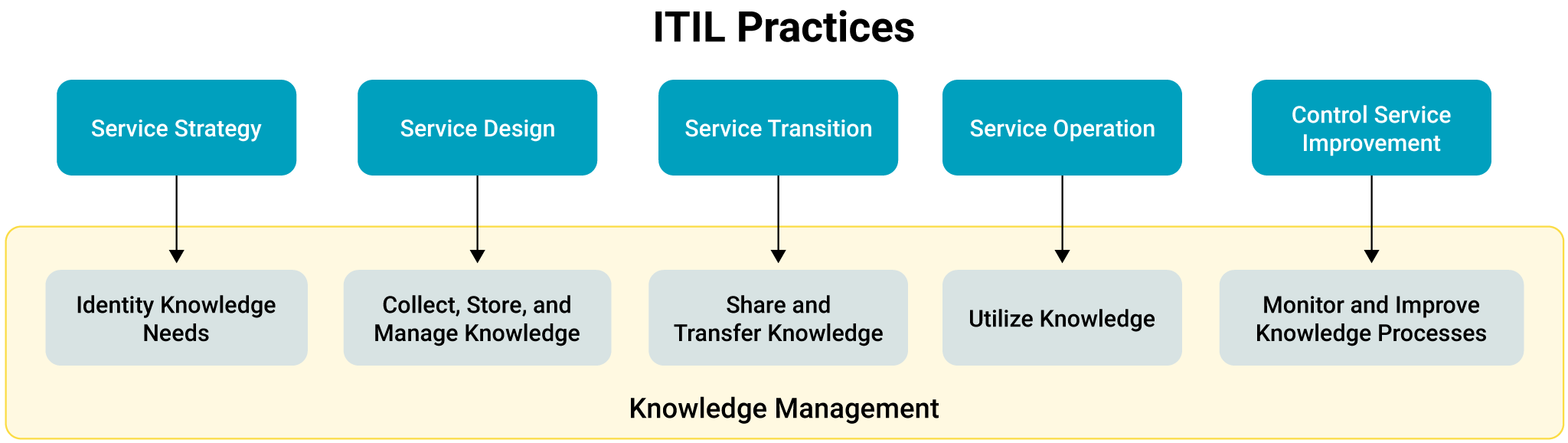
How knowledge management aligns with other ITIL practices
Recommendations
- Start by defining your knowledge management strategy's short- and long-term goals. Consider the business problems the knowledge base aims to solve, then form a management council to plan and explain the goals to everyone involved.
- Establish a structured process for knowledge capture, maintenance, and distribution. For example, IT helpdesk software can automatically convert resolved tickets into knowledge articles.
- Develop templates and an SEO strategy to guide knowledge base indexing for improved accuracy and retrieval.
- Integrate knowledge management into every ITSM process and service lifecycle stage. Although the data within the knowledge base can originate from diverse sources, it is most commonly contributed by subject matter experts based on their experience.
Service Delivery
Although ITSM and IT service delivery might seem synonymous in practice, a subtle distinction exists. A service provides value to the user, but ‘service delivery’ emphasizes service quality, meeting SLAs, and ensuring compliance. Service Level Agreements (SLAs) codify customer expectations and define the relationship between IT service providers and their customers. When uptime is critical and users demand the best, a formalized IT service delivery system helps.
- SLAs should not be limited to external providers but should also govern internal relationships. Establish clear SLAs between IT teams and other departments to ensure everyone understands their roles and responsibilities in supporting business objectives.
- Configure SLA-driven escalations and notifications that go beyond simple alerts. If an SLA breach is imminent, the first notification might go to the assigned technician. If the issue persists, a second escalation could notify their supervisor or a dedicated support team. This ensures that issues don’t slip through the cracks and receive timely attention.
Streamlining workflows with ITSM automation
Automation brings a level of precision and consistency that’s hard to achieve with human intervention alone. A typical approach is automating repetitive tasks that bog down your team, like routing tickets, resetting passwords, or even basic troubleshooting. For IT service technicians, this means spending less time digging through logs and more time-solving critical problems or providing personalized support.
However, the real power of automation comes from integrating different ITSM processes. Set up conditional workflows to create a system that reacts intelligently to different situations. For example, you could automatically escalate a high-priority incident or trigger a change request based on certain conditions.
On an enterprise scale, this level of automation is hard to achieve without specialized tools that leverage structured knowledge and AI-powered technologies like chatbots and virtual agents. These tools act as intelligent assistants, handling routine tasks, answering common queries, and freeing your service desk team to focus on more complex and strategic initiatives.
Planning Your Automation
Don’t just jump into automating your ITSM processes because it seems like the latest trend. Carefully weigh the potential benefits, like faster incident resolution or automated ticket routing, against the costs of implementing and maintaining automation tools. Consider factors like the time saved by your team, reduced errors, and the ability to focus on more strategic work.
Automation works best when your ITSM processes are clear, documented, and consistently followed. Blindly automating inefficient or ineffective processes can amplify existing problems and lead to undesirable outcomes. Before you automate, make sure your processes are well-defined. If your workflows are still largely manual or lack transparency, it’s not the right time to automate. Instead, focus on standardizing and optimizing your processes first to ensure smooth automation implementation.
Implementing Your Automation
Not all automation tools are created equal. Select a solution that integrates seamlessly with your existing ITSM platform and offers the specific capabilities you need, whether it’s workflow automation, chatbot integration, or AI-powered analytics.
When you automate the obvious, do so only in batches. Look for repetitive, time-consuming tasks within your ITSM workflows that have clear steps and predictable outcomes. Automating these tasks first can free up your team quickly and demonstrate the value of automation to stakeholders.
Automation should not be mistaken as a way to eliminate your IT team. It’s essential to have skilled professionals who understand both ITSM best practices and the technology behind automation. Provide training and development opportunities to ensure your team can effectively design, implement, and manage automated workflows for optimal results.
Assess Your ITSM Maturity with the SolarWinds Maturity Model
Beyond mere compliance, organizations should assess the return on investment (ROI) for IT services. Do the services support digital transformation, fuel business growth, and mitigate risks? And crucially, do the services help achieve the goals at an acceptable total cost of ownership?
There are smarter ways to achieve IT excellence, and a top-notch ITSM setup doesn’t have to break the bank.
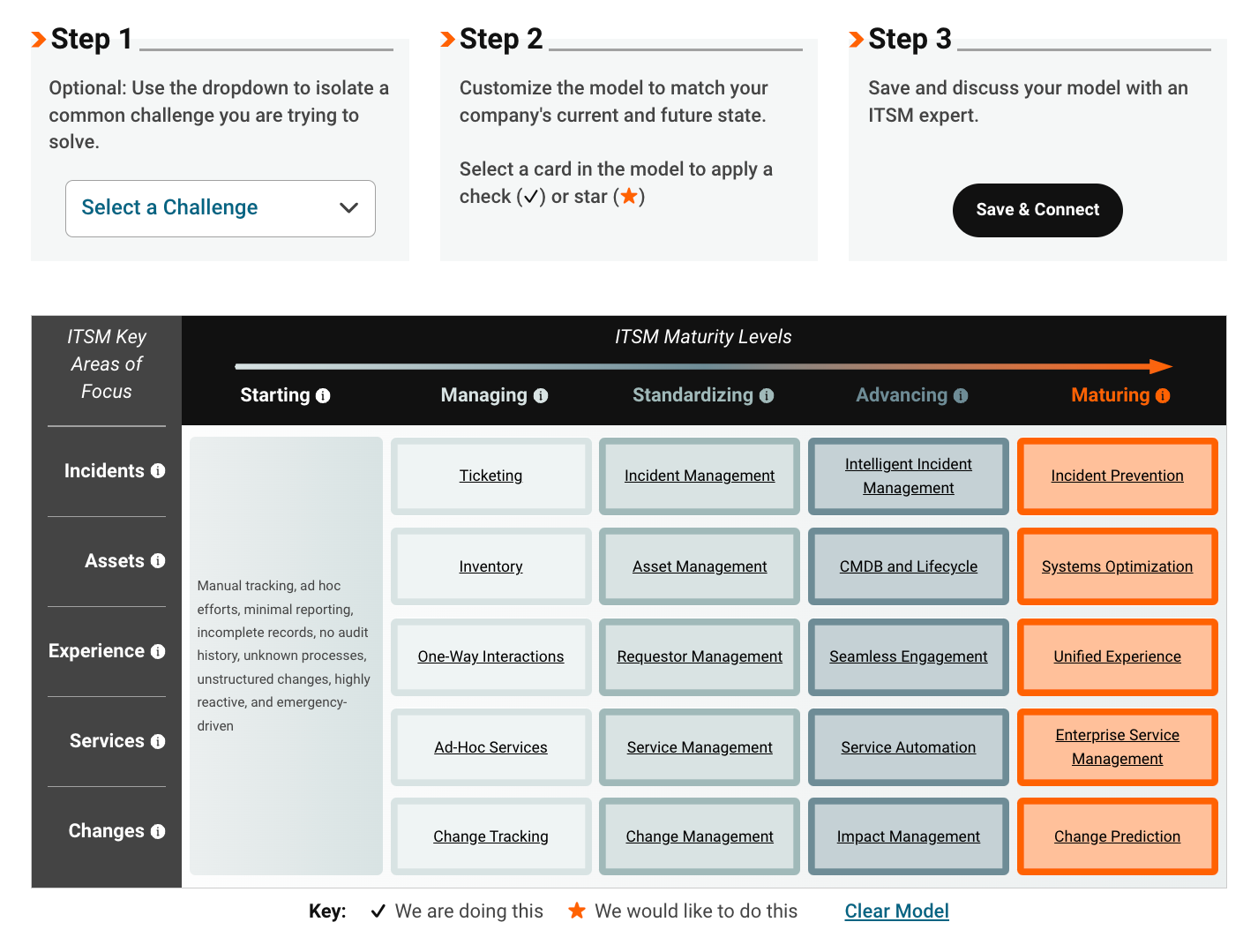
SolarWinds ITSM Maturity Model
SolarWinds has worked with everyone, from small startups to giant corporations, and has poured all that experience into its ITSM Maturity framework. The free, consultative tool is designed to help you figure out your current state, what you intend to achieve, and what tools you need to get there.
Explore our interactive ITSM maturity model here.