Security Monitoring and Observability
Proactively helping organizations identify security threats by analyzing data on a dedicated security dashboard.

Gain visibility into your organization's security posture
Etiam vitae risus suscipit felis imperdiet scelerisque nec euismod ipsum. Aliquam commodo malesuada est a lacinia. Morbi bibendum sapien et risus porta elementum. Phasellus sed consectetur odio, quis egestas tellus.
Single source of truth
Simplify business-critical decision-making based on deeper visibility to system health and security integrity.
Proactive approach
Quickly identify, analyze, and categorize suspicious patterns and anomalies.
Eliminate complexities
Gain insights into the entire internal state of a complex IT distributed system or environment.
Less alert fatigue and silos
Reduce alert fatigue and help eliminate internal silos in both on-prem and hybrid environments and provide an understanding of interdependencies.
Integrated Observability and Security
Our Security Summary Dashboard offers unified visibility into security events across networks, infrastructures, applications, and databases, monitoring your security and compliance status with widgets from SEM, ARM, and Patch Manager.
Gain visibility into security events across networks, infrastructures, applications, and databases.
- Tab 1
- Tab 2
Etiam eu odio a erat gravida bibendum
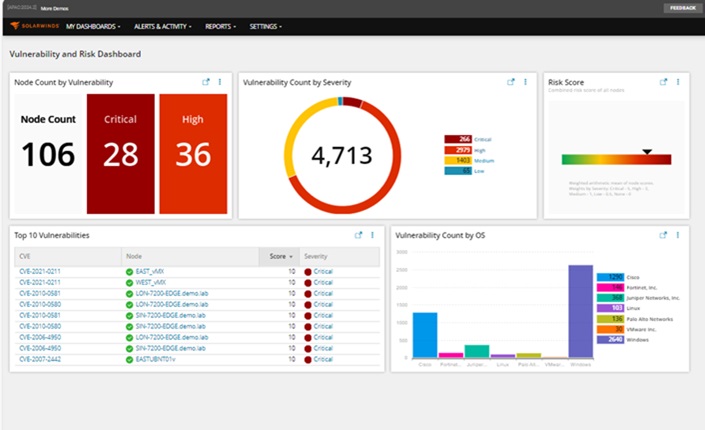
Vulnerability and risk dashboard
Introducing our latest dashboard that enables customers to identify risks in their environment based on vulnerabilities. Vulnerability information is available for Cisco, Juniper, Windows, Linux, and VMware devices.
Etiam eu odio a erat gravida bibendum
Vulnerability and risk dashboard
Introducing our latest dashboard that enables customers to identify risks in their environment based on vulnerabilities. Vulnerability information is available for Cisco, Juniper, Windows, Linux, and VMware devices.
Integrated Observability and Security visibility from a single solution.
Trusted by leading companies




Our security solutions are built to improve IT security and compliance teams' agility, flexibility, and effectiveness
Lorem ipsum dolor sit amet, consectetur adipiscing elit. In vel nunc diam
Self-hosted observability to take you from reactive to proactive across on-prem and hybrid IT environments.
- Deployment to meet your needs, whether behind your firewall or self-hosted in AWS®, Microsoft® Azure, or GCP®
- Flexible licensing – allocate nodes across multiple instances – and optimal scalability
- Built from our years of network management leadership and enhanced with machine learning
Manage and audit access rights across your IT infrastructure.
- Rapidly identify and reduce the risk of unauthorized system access and data breaches
- Easily create user accounts and review user permissions, groups, and access across all systems and data
- Help demonstrate compliance with reports
Improve your security posture and quickly demonstrate compliance with an easy-to-use, affordable SIEM tool.
- Centralized log collection and retention
- Automated threat detection and response
- Integrated compliance reporting tool
You may still have questions.
We definitely have answers.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Duis ullamcorper arcu sed finibus vestibulum. Sed non nibh lectus. Donec lobortis cursus nunc, ac lobortis libero commodo varius.





