Security Event Manager
Improve your security posture and quickly demonstrate compliance with an easy-to-use, affordable SIEM tool.
Starts at
Enhance security and compliance with our intuitive SIEM solution.
Elevate your security strategy with a simple and effective SIEM solution.
Compliance reporting
Advanced compliance reporting with predefined templates for PCI DSS, HIPAA, SOX, and more
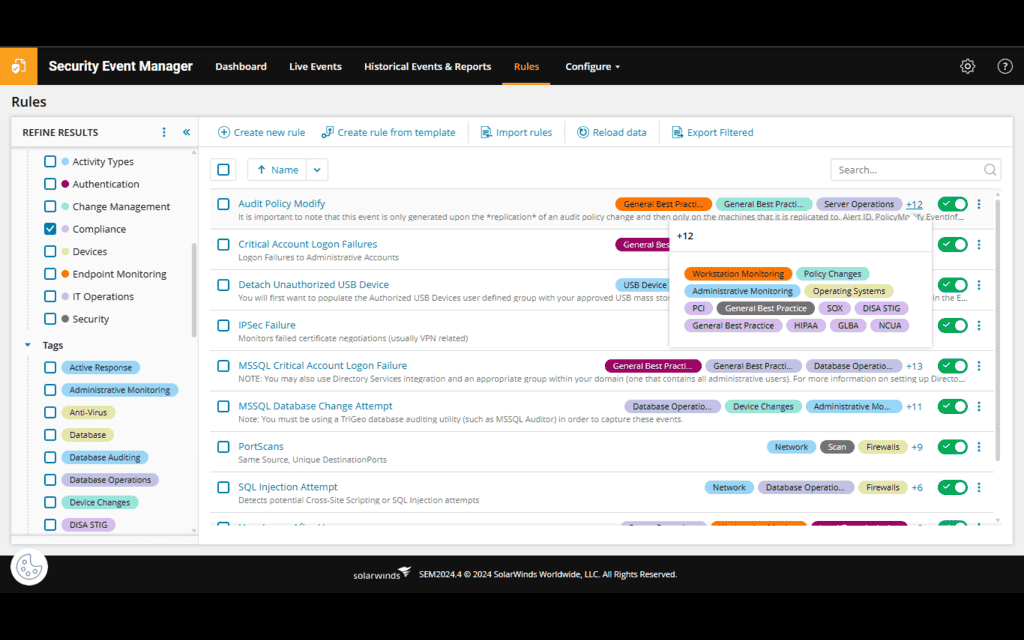
Collect and correlate log data to help satisfy various compliance requirements
Using real-time log analysis and cross-event correlation from sources throughout your entire infrastructure, this compliance monitoring tool can quickly help uncover policy violations, identify attacks, and highlight threats.
Cyberthreat intelligence
A cyber threat intelligence framework is critical for identifying and responding to security threats
Automated incident response
Simplify the incident-response process with security incident management software
Forensic analysis
Get actionable insights from centralized SIEM log data to detect and handle security risks in real time
File integrity monitoring
File integrity monitoring (FIM) protects sensitive information from theft, loss, and malware
Get in-depth insights. Download the datasheet today.
Security Event Manager
Let’s talk it over.
Contact our team. Anytime.




